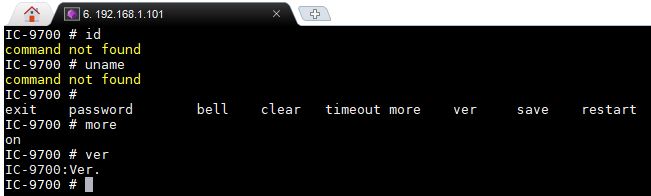
My Icom IC-9700 is connected to the network. And, as a freelance linux and infrastructure (security) engineer, I could not resist to do a port-scan on the box. The first result was port 23, used for the legacy telnet service. Loggin in was easy. No username and password required to get a shell. Quite shocking and a real security risk for devices directly connected to the Internet. That’s a receipe to get hacked within hours.
Since the # would suggest it’s a rootshell, the available commands are quite limited (yet…). But I assume it’s an RTOS shell. I’ll find time to figure it out.

9 comments
Skip to comment form
Wow! That’s pretty bass-ackward on Icom’s part. I’m not sure what could be hacked (besides a restart or a password change) unless there are hidden commands…
Any authentication required? Or just telnet to port 23 and you’re in?
Author
No auth.
Never open firewall ports to your radio, always use a VPN instead. (No matter what other fools tell you).
Why would anyone ever directly connect the radio to the Internet? It should always be behind a firewall with only the specifically required ports opened.
Second page of the manual says:
“This product includes RTOS “RTX” software, and is
licensed according to the software license.
This product includes “zlib” open source software,
and is licensed according to the open source
software license.
This product includes “libpng” open source software,
and is licensed according to the open source
software license.
Refer to the “About the Licenses” page at the end
of this manual for information on the open source
software being used in this product.”
So yes, RTOS RTX.
Good grief. Just because it answers on port 23 doesn’t mean it’s a security problem, and just because the prompt is # doesn’t mean it’s a “root shell.” It obviously isn’t. The interface appears to be extremely limited.
Hi, I’m also digging on that, I found this backdoor because I was trying to investigate why I can’t connecto to the UDP ports for Remote connection, perhaps they are not opne on the router.
This is certainly concerning. However, I would suggest you don’t forward TCP:23 through your NAT/PAT, or allow it to pass your firewall. It doesn’t overly bother me because of that. and WTF is that on TCP:1111?